The demand for Salesforce has skyrocketed over the last decade. Salesforce is the most used CRM platform in the market, and multiple organizations use this to streamline their sales & other business processes. In today’s world, increasing remote work & wide dependence on digital systems force businesses to improve their efforts to preserve the data from both internal & external threats.
Salesforce ensures that the data of customers are safe and implements advanced robust innovations that are required by businesses. However, crucial data comes with multiple significant security responsibilities, and that’s when salesforce security Best Practices come into the frame.
Security testing is crucial in Salesforce CRM to ensure the validation of every data facet. Every business is attracted to successful CRM software since it improves the level of data security. Data protection through the Salesforce Security measures refers to the process of assessing security measures & controls that are implemented within the Salesforce platform for identifying vulnerabilities, risks, and potential weaknesses. Salesforce assurance services ensure that businesses are adequately saved against data breaches, unauthorized access, and additional security threats.
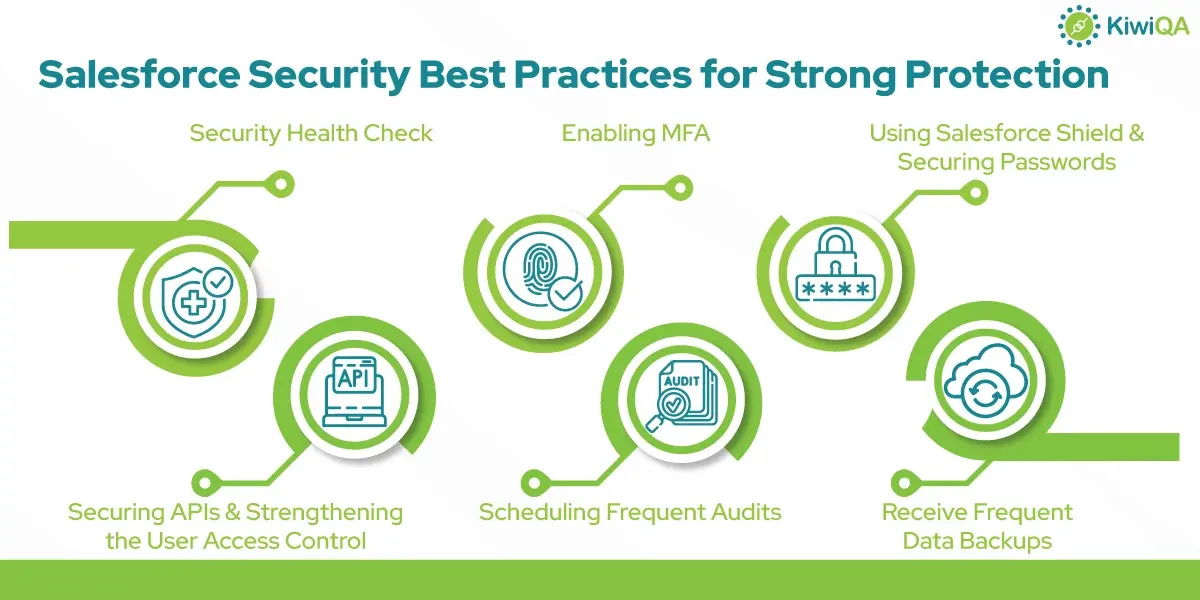
Salesforce Security Best Practices for Strong Protection
Salesforce CRM platforms include sensitive data about business dealings with consumers. Preserving all the data is necessary for business because it can expose lots of data about your company. Salesforce security aids in sustaining the quality and integrity of your business. Organizations must invest their time and resources to guarantee the security of their data. Salesforce CRM doesn’t immune your business to cyber threats even after regular updates and security patches.
Hackers & cybercriminals always actively search for hidden vulnerabilities by employing machine learning & AI. They always look for new ways to hinder security. The most common security risks are unauthorized access, internal threats, and Phishing. There are 3 types of Salesforce security that businesses must use, which are Object-level Security, Record-level security, and field-level security. If it sounds technical, then it will be best to hire an expert.
As the cases of cyber threats are increasing in the industry, businesses are frequently hiring professionals who specialize in this field for security. In the below section, we have discussed the best practices for salesforce testing.
1. Security Health Check
Salesforce health check security is a zero-cost tool that allows admins to manage the organization’s security settings and identify/fix potentially vulnerable security measures. It helps to develop the custom baseline standards that are aligned with the business needs.
2. Enabling MFA
Enabling multi-factor authentication adds an extra layer of safety against threats like credential stuffing, account takeovers, phishing attacks, etc. Through MFA, organizations can improve their salesforce security data.
3. Receive Frequent Data Backups
Interruptions are common in the system, and you need to prepare yourself in case any glitch occurs in the system. Frequent data backups are necessary for recovery and data security. There is a wide range of practices organizations can follow to back up their data. Organizations should also be aware of phishing attempts. Phishing is done by sending false messages to your mail account that further can affect your system and glitch the programs. The best way to save your business from this is to avoid it altogether.
4. Scheduling the Frequent Audits
Frequent audits are necessary because they give data about the system, which is necessary for diagnosing existing and possible security issues. Audits can be carried out either within the organization’s infrastructure or Salesforce. Within the organization, it’s essential to have a designated individual responsible for conducting regular audits to proactively deal with potential threats.
Also Read: How Salesforce Automated Testing Tools Are Shaping the Future?
5. Using Salesforce Shield & Securing Passwords
Through the Salesforce Shield platform, organizations can get a layer of data security for continued functioning. Salesforce Shield is designed to collaborate with admins and developers to support business-critical applications with an extra layer of security. It further allows automation of multiple Salesforce Security. This tool is user-friendly since it doesn’t require any troublesome setup. It protects the sensitive information of organizations.
6. Securing APIs & Strengthening the User Access Control
Salesforce can easily integrate with the other applications & services. It enables a business to share information and support functionalities. Not every application you connect with Salesforce since Salesforce can generate unsecured entries in the process. Users should constantly look into the security model of every API before connecting it to Salesforce to provide access. There are a wide number of default user access settings in Salesforce that users should check to support security when employees are working from home.
Salesforce Data Protection: Encryption & Compliance
When an organization implements the best practices of Salesforce security, it’s necessary to concentrate on Salesforce data protection and privacy. Here are some common data protection compliances you must know:
-
Implementing Data Encryption
Data encryption in Salesforce involves the process of safeguarding data to prevent unauthorized individuals from gaining access. This protective measure is implemented by encrypting the data., it turns into a code that can only decrypt with the keys. People can decipher data without a key, but it’s an extremely complex procedure that requires a wide number of technological resources.
Salesforce security compliance & encryption is the most efficient way to protect data, and it can be used in one of two different schemes, which are Classic encryption and Salesforce shield platform. Salesforce classic encryption utilizes a 128-bit advanced encryption standard, whereas the Salesforce Shield platform uses 256-bit encryption.
The Salesforce Shield platform uses specific algorithms & random patterns for encoding data. It translates the same text into a unique cipher text every time. However, the only drawback of this scheme is that it is complex.
Salesforce can also encrypt data by using the deterministic scheme and lots of organizations prefer this method. This scheme allows organizations to reap the benefits of data filtering. There are not only multiple types of encryption Salesforce scheme, but there are also various data that can be encrypted.
The two primary types of Salesforce data that should be encrypted are data in transit and data at rest. Implementing Salesforce encryption is necessary for organizations to defend their data against unauthorized access. It turns data into unreadable texts and ensures confidentiality.
-
Adhering to Global Data Protection Regulations
GDPR is a strong law for data protection in the EU that updates the existing laws for improving the safety of personal data in terms of rapid technological developments, increasing globalization, and better complex international flow of personal data. It replaces the national data protection laws with a set of rules.
GDPR Salesforce automates the processing that includes the storage and collection of personal data of EU individuals. Every organization that processes Individual data includes tracking online activities within the law. Based on the GDPR the concept of personal data is wide and covers information related to identifiable individuals.
Organizations should utilize necessary organizational and technical security measures for saving data against unauthorized processing, loss, destruction & accidental disclosure. Businesses should follow specific security measures, which are data encryption & segregation, anonymization & pseudonymization. It helps businesses to protect personal data.
Based on the GDPR law, data controllers should report to data protection authorities if there are any data breaches. It shouldn’t be done later than 72 hours after the breach. If the data breaches have high risk then data controllers should address the issues as soon as possible. Non-compliance with regulations by organizations can result in substantial fines and harm the trust of their customers.
Implementing the above-discussed Salesforce data protection plays a strong role in meeting the privacy regulations. By implementing these, an organization can minimize the risks of unauthorized access and ensure compliance.
-
Maximizing Data Security with Salesforce Penetration Testing
Salesforce has become the preferred choice for numerous companies when it comes to handling customer data, making it a top platform for managing your business information. If you’re looking to safeguard your business data confidential, then you must strengthen the business against threats. Whether you have leveraged your business with Salesforce recently or for a while, it is crucial to stay aware of the potential glitch and address them before it turns into the biggest threat.
Salesforce penetration testing is one of the effective ways to maximize data security.
Penetration testing, also known as pen testing, aids organizations in uncovering their vulnerabilities and weaknesses. Pen testing aims to find creative solutions to end the vulnerabilities. So, the goal is to identify a threat factor that might harm the credentials of the business.
Also Read: Top 6 Common Challenges in Salesforce Testing
Penetration testing offers an independent assessment of security salesforce deployment. The testing helps organizations to find out the weaknesses during the deployment and ensures a promising effective solution. This is an excellent way to ensure compliance with contractual requirements and regulations like payment card industry data security standards and general data protection regulations. It gives an additional layer of security.
By implementing this, businesses can measure the vulnerabilities and eliminate the data breach risk. If you want to safeguard the salesforce implementation, then penetration testing is necessary. Salesforce penetration testing detects & fixes vulnerabilities. By implementing proactive measures, you can bolster the organization’s security stance and shield it from possible threats.
Role of Salesforce Security Audit in Strengthening Data Defence
Data audits are necessary to ensure the quality and integrity of data. Data audits are necessary for identifying the errors, duplicacy, and inconsistency in the Salesforce database. Salesforce security audits impact the accuracy of reports and the effectiveness of business processes. If a business wants to ensure the best out of its investment, then it should adopt a salesforce security audit. Through a salesforce security audit, businesses can defend their system to diagnose potential security issues.
Salesforce data audits help to address and fix issues with data quality like errors, duplicates, and inconsistency. Through this, businesses can enhance their efficiency since they are working with reliable data. Data inaccuracies can lead to compliance issues and decision-making abilities. If you are audited, and the data requires correction, then you may be subjected to penalties. Here, we are discussing various types of Salesforce data audits that can be conducted.
-
Data Completeness Audit
Through this, the businesses can inspect the missing data in the salesforce database. It helps to address the data gaps and also enhances the accuracy of decision-making and reporting.
-
Data Accuracy Audit
This audit procedure is carried out to detect errors & data inconsistencies. It audits incorrect spelling and formatting and detects data that doesn’t meet the organization’s standards.
-
Auditing Data Duplicates
An organization carries out this procedure to check the duplicate records in the salesforce database. Data duplicates cause issues in reporting and also impact the business efficiency processes.
-
Data Security Audit
The Salesforce security audit addresses the security vulnerabilities in the Salesforce database. It includes tracking unauthorized data access, potential security vulnerabilities, and weak passwords.
As an organization grows and the regulation changes, it becomes tough to prepare audits, and that’s when you can get help from an expert.
How Risk Assessment Works in Salesforce Environments?
Here is how salesforce risk assessment works-
-
Risk Identification
If you plan to identify the risks, proceed with evaluating the hazards. Determine what hazards your business, including all aspects of activities. The reason could be anything from technical hazards to supply chain interruptions and from natural disasters to workplace accidents. After this, evaluate who might be harmed by this and how. Once you identify the potential risks and individuals who might get harmed, move to the next step.
-
Risk Evaluation and Management
Now, it’s time to evaluate the potential risks which you have measured. Determine how severe the consequences will be so that you can reduce the risk level and which risk should be prioritized first. Create the risk assessment chart to ease the process. Write down the risk assessment procedure you are following. At the end, review the assessment and update if it’s necessary.
Your workplace is in a constant state of flux, which means that the risk landscape for organizations is constantly evolving as well. Once you evaluate all the risks, utilize the treatment plan. Set up the risk management process by prioritizing them.
Address each issue individually or take steps to eliminate the risks, ensuring they no longer pose a threat to the project. Monitor the potential threats and send regular updates to the team. Take help from the risk managers to ensure there are not any more red flags that may pop up throughout the project.
Protect Data: Salesforce Security Framework
Salesforce security framework assists you in saving information at multiple levels. The organization fields, records, and objects are the logistic security tiers. To use the Salesforce security framework, the organization needs to follow the following layers to safeguard the organization. Here is a short view of the security framework that organizations should build the data protection measures-
-
Security Based On Organizations
Organizational security contains an evaluation of who can access the Salesforce organization. Users could utilize the IP limitations to restrict the IPs that can be used for login by the customers.
-
Object Level Security
It evaluates who can get access to the object. Utilizing object-level security to get access to a specific domain by delivering multiple accounts on profile.
-
Security Based on Fields
Authorizations and profile sets also measure the user’s access to fields. It is beneficial whenever you require a user to get access to the object and limit their power, modify, and edit.
-
Security Based on Record
It controls the data of customer access. To control record access, organizations should follow certain ways, which are manual sharing and role hierarchically.
This is how the Salesforce framework supports Salesforce’s overall security architecture.
Take Your Salesforce CRM to the Next Level with Expert Testing!
When it comes to the protection of data, understanding salesforce CRM security features and benefits is what matters a lot. Security testing is an ongoing procedure that requires regular assessment to get the best. By performing the security testing, the salesforce organization can address and identify the security vulnerabilities/risks.
Salesforce CRM security testing enhances overall security and maintains a robust security environment. If you are running a business and you want to stay away from various security threats, you should improve & strengthen the CRM security practices by hiring salesforce CRM testing services. With the expert’s help, you can maintain the credibility of your business.